Two factor / Multi factor authentication
Flex2B has an integration for multi-factor web user authentication embedded in the solution. It can be enabled in general and per individual user indicated whether (s)he needs the 2FA or MFA ability.
Authentication will then be done by a TOTP mechanism that generates a time based code every x seconds (in general every 30 seconds).
What is MFA in brief?
MFA stands for Multi-Factor Authentication, which is a security mechanism used to enhance the protection of accounts and systems by requiring users to provide multiple forms of verification before granting access. The goal of MFA is to add an extra layer of security beyond just a traditional username and password combination.
MFA typically involves three factors of authentication:
Something You Know: This is typically your username and password combination. It's the most common form of authentication but is often considered insufficient on its own due to the vulnerabilities of passwords (e.g., weak passwords, password reuse, etc.).
Something You Have: This refers to a physical or digital item that only the legitimate user possesses. This could be a smartphone, a hardware token, a smart card, or a temporary code sent via SMS or email.
Something You Are: This involves biometric factors such as fingerprint scans, facial recognition, or iris scans. These physical characteristics are unique to each individual and are difficult to forge.
To access a system or account protected by MFA, a user would need to provide at least two of these factors. For example, after entering their username and password (something they know), they might also need to input a code sent to their smartphone (something they have) or use their fingerprint (something they are) to complete the authentication process.
MFA significantly enhances security because even if a malicious actor obtains your password, they still wouldn't be able to access your account without the additional factor. This approach greatly reduces the risk of unauthorized access due to stolen passwords or phishing attacks.
MFA is widely used across various platforms, including online services, banking, email, social media, and corporate networks, to provide an extra layer of protection against unauthorized access and data breaches.
Most modern mobile devices have a 2D-barcode scanner in it embedded. This can be used to scan at the first occurence a QR-code, that can be embedded in the verification tool or your mobile app.
Looking at the instance that corresponds with you, you will get a temporary time based 6-digit code that needs to be entered in the Flex2B login form for the 2FA/MFA/TOTP code form upon login.
As an example, we show a verification code on MS Authenticator on a mobile device, however, there is a wide range of the client tools available in the App-Store or Play-store of your mobile device (iOS / Android).
The 6-digit code in the blue is switching every x (30), seconds. You need to enter this code in the compared time frame and click the login button in that time frame.
Note. If you can not enter it in time, just wait, because a next code will be offered to you.
Please consult your own IT department to get suggestions on the Authenticator tools that they are supporting or contact the App-Store or Play-store of your mobile device.
The authenticator tool needs to be logged in manual or by a biometric implementation (finger print, face recognition, ...)
Sample:
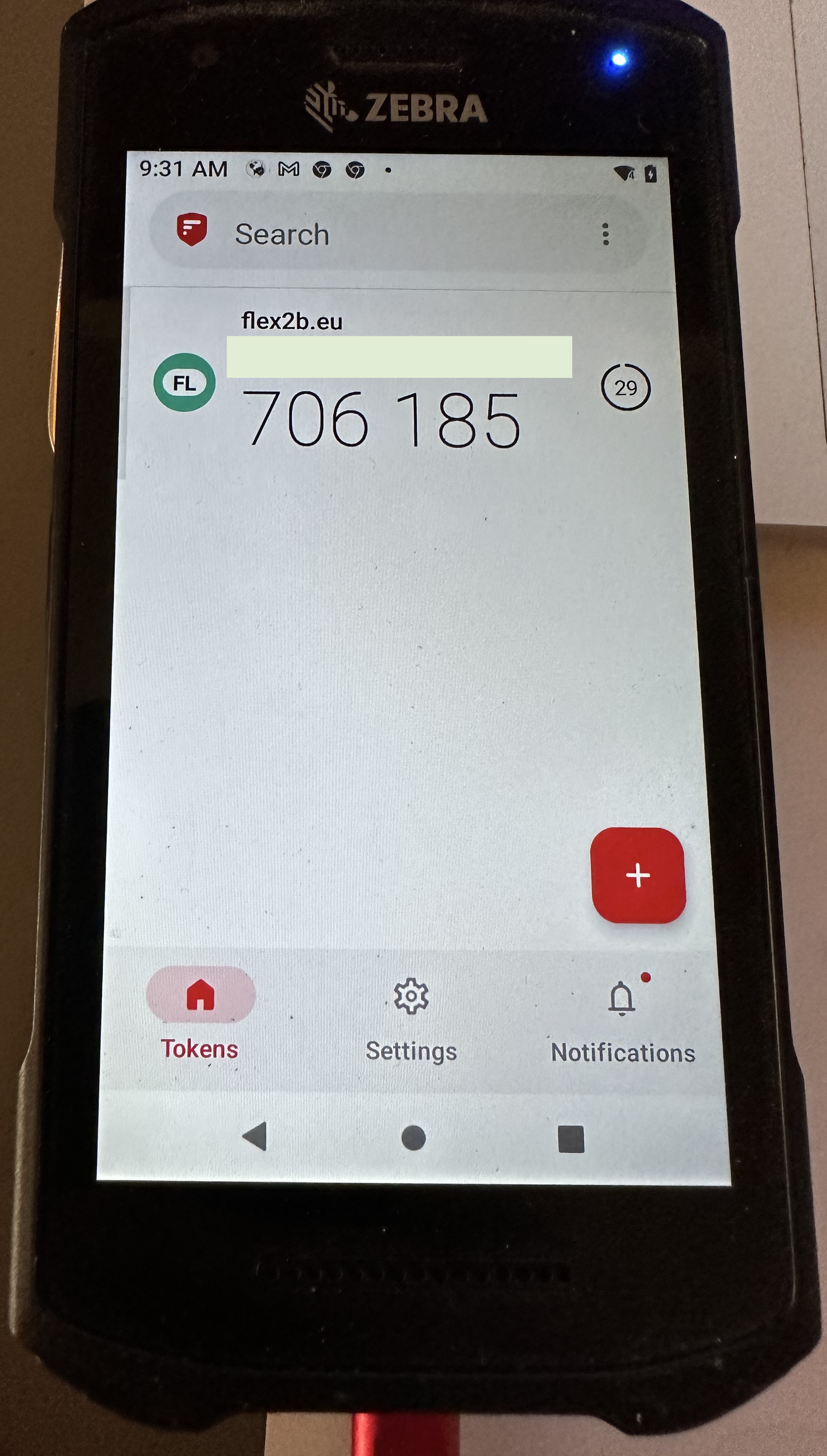
On Android via a 3rd party verification app from the Android Play Store: (2FAS - provided as sample). You seen the timed access token for the user.
You can choose a variety of authentication apps.Screenshotting from Android was forbidden by the vendor, so a simple photo as an example.
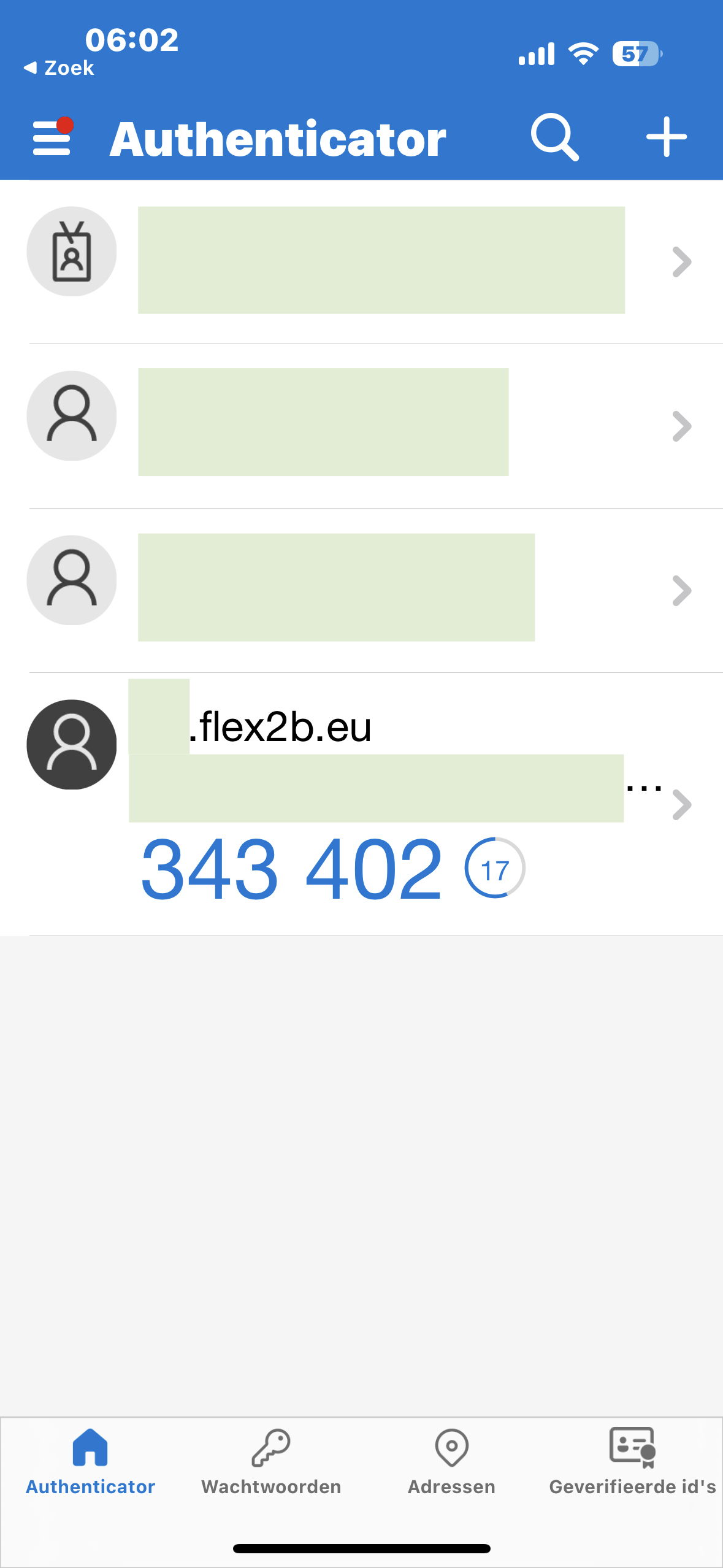
On iPhone via a 3rd party verification app from the App Store. (Microsoft - provided as sample). You seen the timed access token for the user.
You can choose a variety of authentication apps.
Important note.
Even when a 2FA verification is enabled, a user password that complies with the company security policy is needed.